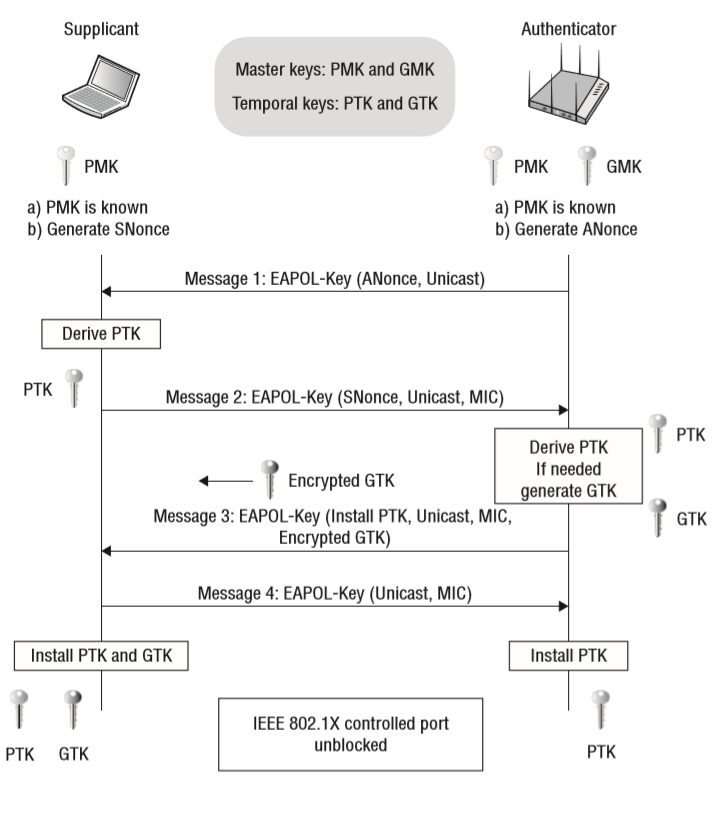
4 Way Handshake
4 Way Handshake
Message Flow
The 4-way handshake is the process of exchanging 4 messages between an access point (authenticator) and the client device (supplicant) to generate some encryption keys which can be used to encrypt actual data sent over Wireless medium [1].
Message1: access point sends EAPOL message with Anonce (random number) to the device to generate PTK. Don’t forget client device knows Ap’s MAC because its connected to it. It has PMK, Snonce and its own MAC address. Once it receives Anonce from access point it has all the inputs to create the PTK.
PTK = PRF (PMK + Anonce + SNonce + Mac (AA)+ Mac (SA))
Message2: Once the device has created its PTK it sends out SNonce which is needed by the access point to generate PTK as well. The device sends EAPOL to AP message2 with MIC (message integrity check) to make sure when the access point can verify whether this message corrupted or modified. Once SNonce received by the AP it can generate PTK as well for unicast traffic encryption. This is the second message going from the client device to AP with Snonce and MIC field set to 1.
Message3: EAPOL message3 is sent from AP to client device containing GTK. AP creates GTK without the involvement of the client from GMK.
Message4: Fourth and last EPOL message will be sent from the client to AP just to confirm that Keys have been installed.
4 Way Handshake Result
Control port unlocked: Once the 4-way handshake is completed successfully virtual control port which blocks all the traffic will be open and now encrypted traffic can flow. Now all unicast traffic will be encrypted with PTK and all multicast traffic will be encrypted via GTK which created in the 4-way handshake process.
Deauthentication Reason Code Table
The following table describes the deauthentication reason codes
| Code | Meaning |
|---|---|
| 0 | Reserved. |
| 1 | Unspecified reason. |
| 2 | Previous authentication no longer valid. |
| 3 | STA is leaving or has left IBSS/ESS. |
| 4 | Disassociated due to inactivity. |
| 5 | AP cannot handle all currently associated STAs. |
| 6 | Class 2 frame received from nonauthenticated STA. |
| 7 | Class 3 frame received from nonassociated STA. |
| 8 | STA is leaving or has left BSS. |
| 9 | STA requesting (re)association is not authenticated. |
| 10 | Power Capability element is unacceptable. |
| 11 | Supported Channels element is unacceptable. |
| 12 | Disassociated due to BSS Transition Management. |
| 13 | Invalid element (does not meet Clause 8 specs). |
| 14 | MIC (Message Integrity Code) failure. |
| 15 | 4-Way Handshake timeout. |
| 16 | Group Key Handshake timeout. |
| 17 | Element in 4-Way Handshake inconsistent with other frames. |
| 18 | Invalid group cipher. |
| 19 | Invalid pairwise cipher. |
| 20 | Invalid AKMP. |
| 21 | Unsupported RSNE version. |
| 22 | Invalid RSNE capabilities. |
| 23 | IEEE 802.1X authentication failed. |
| 24 | Cipher suite rejected due to security policy. |
References
[1] https://www.wifi-professionals.com/2019/01/4-way-handshake
[2] https://www.cisco.com/assets/sol/sb/WAP371_Emulators/WAP371_Emulator_v1-0-1-5/help/Apx_ReasonCodes2.html
This post is licensed under CC BY 4.0 by the author.