Social Engineering
Understanding Social Engineering Attacks
Social engineering is the art of manipulating people’s psychology to reveal confidential information or perform actions that benefit the attacker.
1. Common Types of Social Engineering
A. Impersonation
This is the most common human-based social engineering technique.
Mechanism: The attacker pretends to be a legitimate or authoritative person.
Method: Performed in person (face-to-face) or through media such as phone calls, emails, etc.
Objective: To trick the victim into revealing sensitive information.
B. Phishing
Phishing is the act of sending invalid emails impersonating reputable websites/organizations to steal users’ personal information or account details.
Types of Phishing:
Spear Phishing: A targeted attack on a specific individual or organization.
Whaling: Targeting “big” targets such as CEOs or senior managers.
Pharming: Attackers install malicious software to redirect web traffic from a legitimate site to a fake website.
Spimming: Phishing attacks via instant messaging.
Tools to Support Phishing:
The Social-Engineer Toolkit (SET): A powerful toolset for simulating attacks.
ShellPhish: An automated tool for creating fake pages.
2. Other Computer-Based Social Engineering Techniques
Attackers use software and computer interfaces to deceive users:
Pop-Up Windows: Fake notification pop-ups.
Hoax Letters: Scam emails (e.g., fake prize notifications).
Chain Letters: Misleading or promising forwarded emails.
Instant Chat Messenger: Online messaging scams.
Spam Email: Spam containing malicious content or fraudulent advertisements.
Scareware: Scary software (e.g., fake virus alerts) to force users to install malware.
3. Practice with Social-Engineer Toolkit (setoolkit)
SET tools are often used in lab exercises to demonstrate attack capabilities:
- Creating Web Clones: Copying the interface of a popular website (such as Facebook, Gmail) to steal login information when the victim enters it into the fake page.
4. Mobile Application Attacks
Attackers exploit users’ trust in app stores:
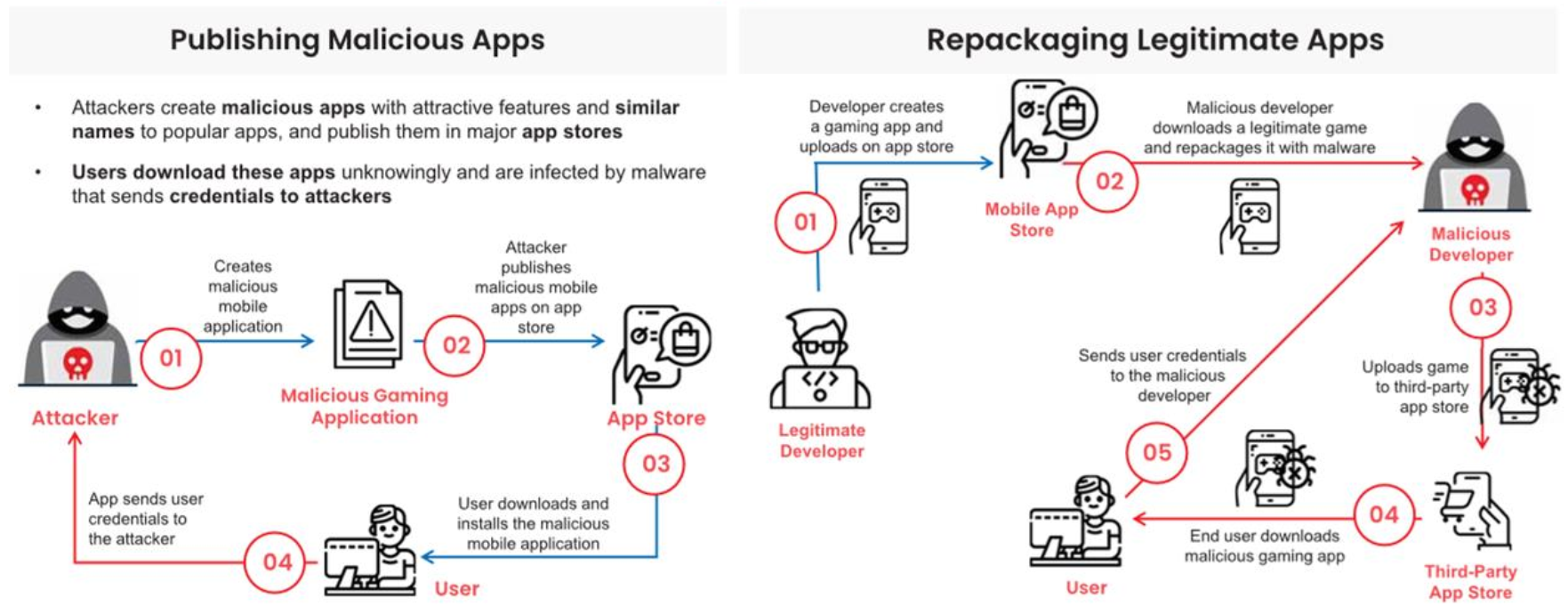
Publishing Malicious Apps: Releasing applications containing malicious code directly to the store.
Repackaging Legitimate Apps: Taking legitimate applications, inserting malicious code inside, then repackaging and distributing them to steal user data.
Publishing Malicious Apps and Repackaging Legitimate Apps
—Note: This document is for educational purposes and to raise awareness about information security.