Virtual Private Network
Virtual Private Network
What is the VPN?
VPN stands for the Virtual Private Network. A virtual private network (VPN) is a technology that creates a safe and encrypted connection over a less secure network, such as the internet.
A Virtual private network (VPN) is a secure connection between two or more endpoints. It can also be seen as an extension to a private network.
A VPN is commonly used to provide secure connectivity to a site in order to share resources between two organisations or departments or to facilitate remote users with their corporate services as if they were in sitting at their desk in the office. There are two key scenarios where you would deploy VPN technology, that are known as Site-to-Site VPN and Remote Access VPN.
Site-to-Site VPN
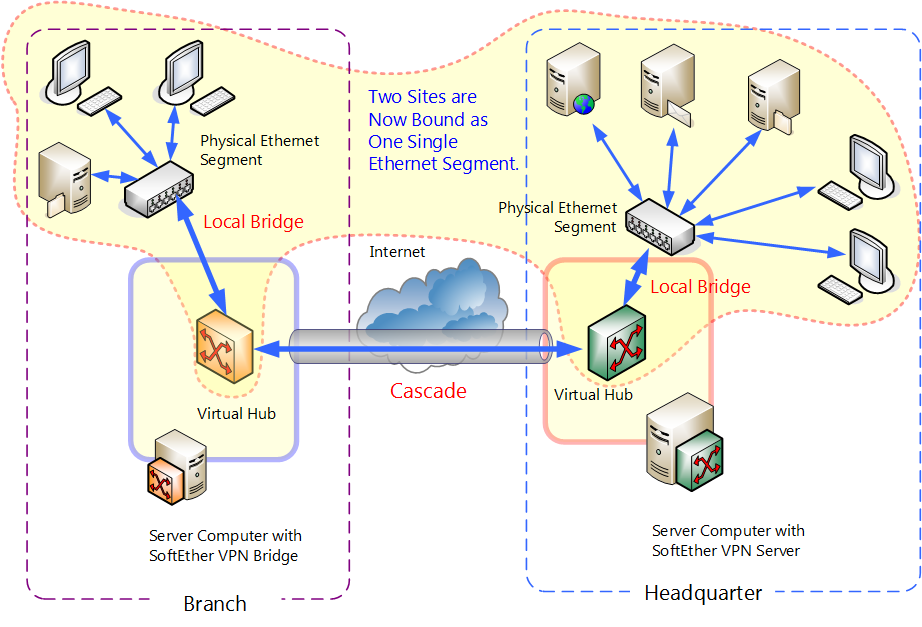
In site-to-site VPN, data is encrypted from one VPN gateway to another VPN gateway, providing a secure link between two sites organisations departments over the internet. This would enable both sites to share resources such as documents and other types of data over the secure VPN link.
The following figure illustrates a site-to-site VPN deployment, where an organisation has two offices and would like to provide a secure VPN link between the two offices to share resources.
Remote Access VPN
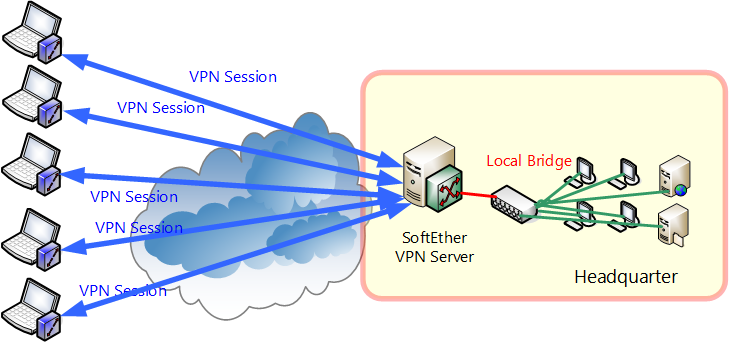
In a remote access VPN scenario, which is sometimes known as mobile VPN, a secure connection would be made from an individual computer to a VPN gateway device that is situated at the organisation's data centre.
This VPN device would enable a user to access their e-mail, files and other resources at work from anywhere in the world, providing they have an internet connection.
There are two common forms of frameworks technology that exists in remote access VPN known as IPsec and SSL that are covered further within this article.
The following figure illustrates a remote access user VPN deployment.
Why is VPN?
Consider a scenario where the corporate office of a bank is located in Washington, USA. This office has a local network consisting of say 100 computers. Suppose other branches of the bank are in Mumbai, India, and Tokyo, Japan.
All 100 hundred computers of the corporate office at Washington are connected to the VPN server(which is a well-configured server containing a public IP address and a switch to connect all computers present in the local network i.e. in US head office).
The person sitting in the Mumbai office connects to The VPN server using a dial-up window and the VPN server returns an IP address that belongs to the series of IP addresses belonging to a local network of the corporate office.
Thus person from the Mumbai branch becomes local to the head office and information can be shared securely over the public internet.
So this is the intuitive way of extending the local network even across the geographical borders of the country.
How to VPN work ?
A VPN works by routing a device's internet connection through a private service rather than the user's regular internet service provider (ISP). The VPN acts as an intermediary between the user getting online and connecting to the internet by hiding their IP address.
VPN Protocols
Point-to-Point Tunneling Protocol (PPTP)
PPTP is one of the oldest protocols still active on the internet. Created by Microsoft, it uses the Transmission Control Protocol (TCP) control channel and Generic Routing Encapsulation (GRE) tunneling protocol. It relies on the Point-to-Point Protocol (PPP), which is a Layer 2 communications protocol directly between two routers, to implement security functionalities.
PPTP is fast and simple to deploy but only really applicable to people using older Windows operating systems. It also has several well-known security issues, so any VPN that only uses PPTP should be avoided.
Layer 2 Tunneling Protocol (L2TP)
This protocol combines PPTP with the Layer 2 Forwarding (L2F) tunneling protocol. It strengthens the data tunnel provided by PPTP but does not provide users with encryption or privacy capabilities. As a result, the protocol is typically bundled with a security protocol such as Internet Protocol security (IPsec).
IPsec (IP Security)
IPsec operates at layer 3 of the OSI model and for this reason can protect any protocol that runs on top of IP.
IPsec is a framework consisting of various protocols and algorithms which can be added to the framework.
IPsec provides flexibility and strength in depth, and is an almost perfect solution for securing VPN tunnels.
The only drawback to IPsec is it requires setting up on the corporate network and on the client side devices, and is a complex framework to work with. IPsec is used for both site-to-site and remote user VPN connectivity.
Secure Socket Layer (SSL) VPN
SSL VPN provides excellent ease of use, flexibility and security for remote access users. SSL is already heavily used such as when you shop online, and when accessing your bank account online, you will notice an SSL protected page when you see the “https” in your browser URL bar.
Secure Socket Tunneling Protocol (SSTP)
SSTP is a VPN tunnel created by Microsoft and is a much more secure option. It transports PPP traffic through the secure sockets layer/transport layer security (SSL/TLS) channel, which provides encryption, key negotiation, and traffic integrity checking. As such, only the two parties that transmit the data are able to decode it. Using this over the TCP port 443 ensures that SSTP can travel through most firewalls and proxy servers.
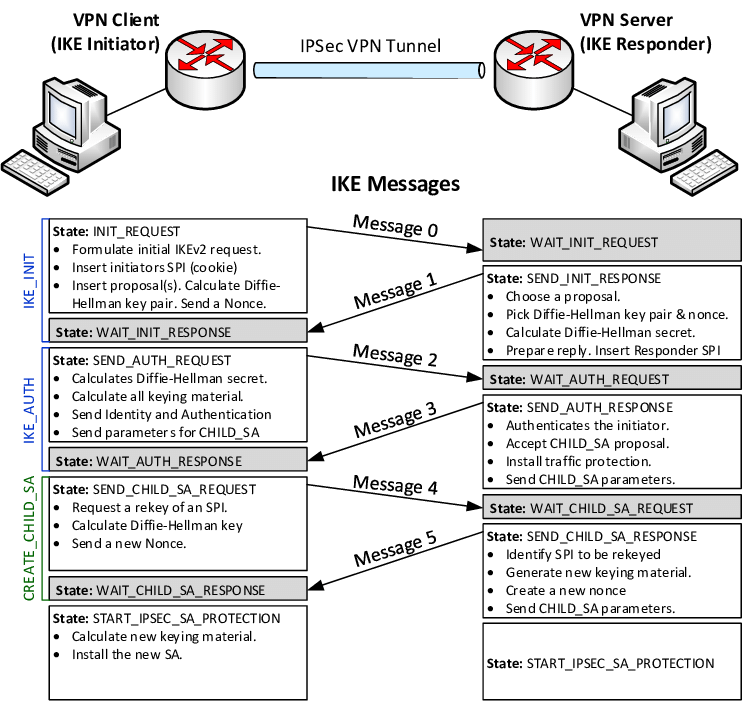
Internet Key Exchange Version 2 (IKEv2)
IKEv2 handles request and response actions to ensure traffic is secure and authenticated, usually using IPsec. It establishes the security attributes of the device and server, then authenticates them, and agrees which encryption methods to use. It supports 256-bit encryption and allows the use of popular ciphers such as Advanced Encryption Standard (AES), Camellia, and ChaCha20. IKEv2 is mostly used to secure mobile devices, in which it is particularly effective.
OpenVPN
OpenVPN is widely considered the best open-source VPN technology available. The free software uses pre-shared certificates, secret keys, and usernames and passwords to authenticate every device or server. It uses the open secure sockets layer (OpenSSL) encryption library and TLS, in addition to a custom protocol utilizing SSL/TLS for key exchange. OpenVPN offers the same protection as established protocols but on a wider scale.
Setting up an IPsec Site-to-Site VPN Tunnel
To start with, you would need to decide how you are going to authenticate both VPN peer devices to each other. You need to either agree upon a Pre-shared key or install digital certificates. This is used for authentication and to ensure the VPN gateway devices are authorised. This would prove their identities to each other. Both gateways must use the same type of credentials, so either both sides will use pre-shared keys or both sides will use digital certificates. Also if you are using pre-shared keys, then both keys would have to match.
VPN's are configured and processed in two phases, phase 1 and 2.
Phase 1
In phase 1, you would use Main mode or Aggressive mode to set up a secure and encrypted channel, to protect your phase 2 negotiations.
You will need to specify both gateway addresses. At each end, you would specify the address of the local VPN gateway and you would also specify the address of the remote VPN gateway. You can either specify an IP address or a domain name. On some VPN gateway devices you could also specify an e-mail address, or if you use a digital certificate, you could specify the certificates subject field.
Main mode or aggressive mode can be selected depending on which one you would want to use and depending upon the type of VPN and how IP addresses are assigned. Main mode is more secure, but slower than aggressive mode. In Main mode peers exchange identities and protect the exchanges with the use of encryption, and with Aggressive mode, although faster, exchanges identities without encryption (in clear text). Main mode is the more commonly used option. Aggressive mode is typically used for when one or both of the VPN gateway devices have dynamic IP addresses or when it's a remote access VPN connection. Most common method when setting up site-to-site VPN tunnels is Main mode, unless as already explained, when dynamic IP addressing is used.
Specify whether to use Nat-Traversal. This is selected if your VPN gateway is behind a NAT device. Specify whether you want both peers to use IKE keep-alive. This ensures that if a VPN gateway device interface is not responding to keep alive requests, it will failover to the second interface (if this has been setup). This is true when you have multiple connections to the internet and both are used to provide VPN connectivity. When the primary ISP connectivity fails the backup secondary link becomes the active link for the VPN tunnel.
You would now configure the VPN proposalstransform sets. This includes the type of encryption, authentication, Hashing algorithm and the security association timeout values. Typically for authentication, you would choose to use either a pre-shared key or digital certificates and two of the common options when choosing a hashing algorithm are Sha or MD5. Sha is the stronger of the two algorithms.
For encryption the following are some of the common encryption algorithms, which include DES, 3DES or AES 128, 192, 256 bit key strengths. AES is the strongest protocol of the ones mentioned.
You can specify a limit before your Security Association (SA) expires, which will add further protection to the VPN if your keys have been compromised hacked. Although, do consider, the more secure and the more options turned on, this will have an effect on performance and could complicate maintenance and troubleshooting.
You will need to specify a Diffie-Hellman key group, usually 1, 2, 5 or 14 or higher, in which the higher the key chosen is the more secure group.
You can optionally set up extra proposalstransform sets if needed. If you’re not sure on your peers proposal settings, then you may want to set up a number of proposals transform sets, using algorithms that are acceptable to use. Although it is recommended to know your peers settings and create the minimum proposals required as it is more secure this way.
Phase 2
In phase 2, using Quick mode, you would establish the IPsec Security Association (SA). Here, you would tell the gateway what traffic you will be sending over the VPN, how to encrypt and authenticate it.
You will need to specify what traffic will go across the VPN. So you would be specifying an IP address, Network address, or IP address range. This is access to your internal network, so either remote users from home, or the peer office can have access to resources behind the VPN gateway.
You can choose whether to use Perfect forward secrecy (PFS), for optional and an extra layer of security. If you will be using PFS, remember that both VPN peers must support and use PFS. You can select which Diffie-Hellman group to use for new keying material. The higher the group you select, the stronger the key. You would now need to specify some more parameters in securing your data within the IPsec SA (Phase 2), also known as phase 2 proposals. The parameters are made up of encryption and authentication algorithms.
Here you first specify the type of proposal, either selecting AH or ESP. AH only provides authentication, and ESP provides authentication and encryption.
If you have specified ESP, which the majority would choose, then you would specify your authentication and encryption. For authentication and integrity you can select SHA or MD5, where SHA is the strongest algorithm of the two. For encryption you can select DES, 3DES or AES 128, 192, or 256-bit key strengths. AES 256 is the strongest encryption protocol of the ones mentioned.
You may want to specify a value for when your key would expire. This would ensure your encryption keys would change over a period of time, adding more security, as well as having a slight effect on performance. The majority of organisations leave these settings as the default, however if you are a bank or any other company dealing with highly sensitive and confidential data then you may want to force keys to expire, and have them re-created.
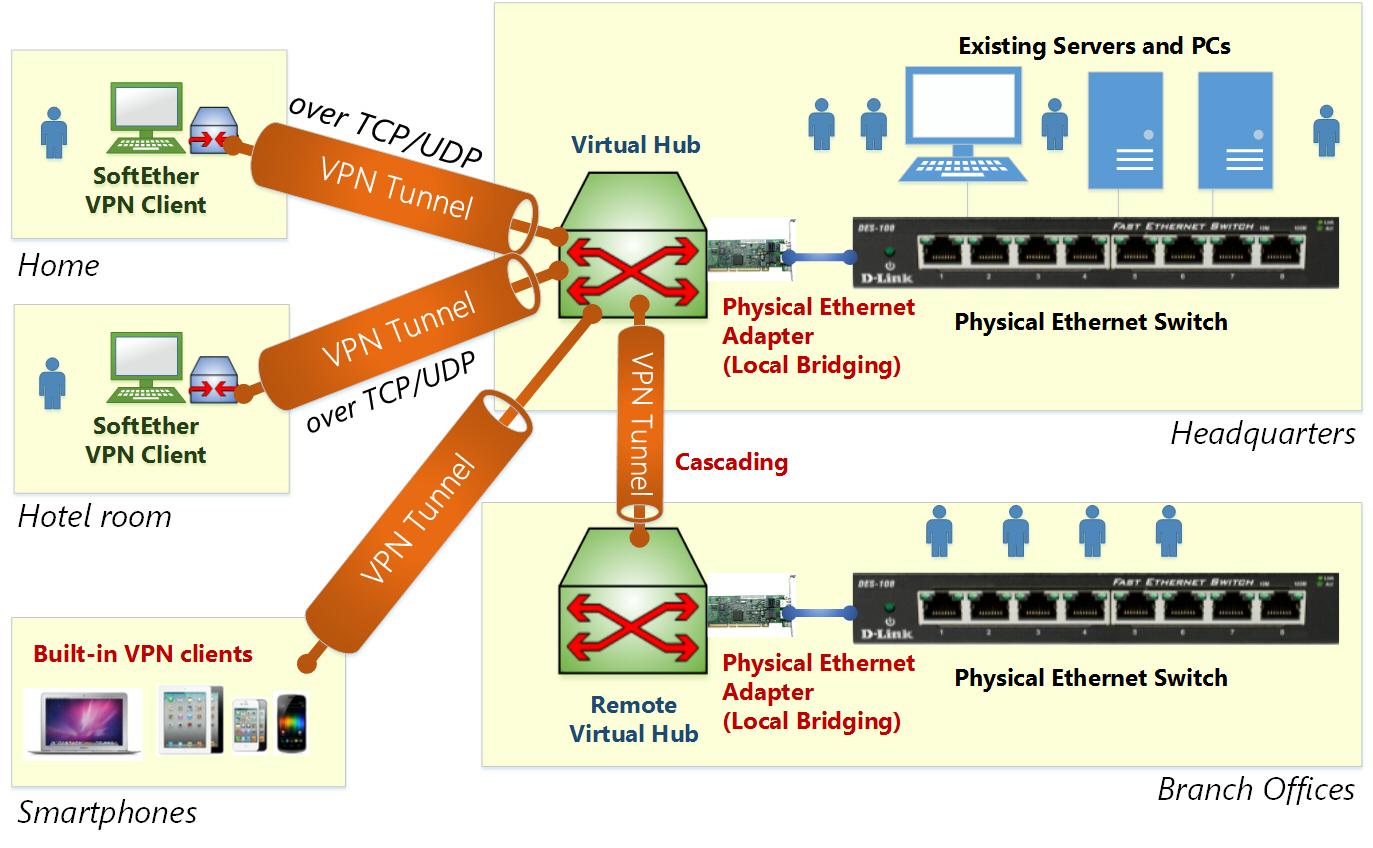
Scenario
References
[1] https://www.softether.org/1-features
[2] https://www.researchgate.net/figure/The-IKEv2-exchanged-packets_fig2_323135410
This post is licensed under CC BY 4.0 by the author.