WPA3
WPA3
What Is WPA3?
Wi-Fi Protected Access 3 (WPA3) is a next-generation Wi-Fi (WiFi) encryption protocol released by the Wi-Fi Alliance in 2018. It introduces a variety of new functions based on WPA2, providing more powerful encryption protection for data transmitted between users and Wi-Fi networks. Based on application scenarios and security requirements of Wi-Fi networks, the following WPA3 modes are available: WPA3-Personal, WPA3-Enterprise, and Opportunistic Wireless Encryption (OWE).
WPA3-Personal: Enhanced Password Protection
WPA3-Personal can work in two modes:
- WPA3: WPA3 mode to use SAE protection and implement the use of Protected Management Frames (PMF). This mode requires wireless clients to support WPA3 mandatorily
- WPA3 Transition Mode: WPA3 transition mode can handle the capability to use SAE and PMF and also allows WPA2 clients to co-exist on the same SSID if the clients do not support WPA3-SAE.
WPA3-Personal uses Simultaneous Authentication of Equals (SAE) to replace PSK authentication in WPA2-Personal.
In WPA2, PSK authentication involves a 4-way handshake for key negotiation. Before the negotiation, a PMK is generated based on the service set identifier (SSID) and PSK, which are both fixed. Therefore, the generated PMK is fixed and can be calculated. As a result, the same key is used for each reinstallation. The SAE protocol used by WPA3 adds an SAE handshake before the original PSK 4-way handshake and introduces a dynamic random variable in the PMK generation process. Therefore, the PMK negotiated each time is different, ensuring the randomness of the key. As such, SAE provides a more secure key authentication mechanism for WPA3 to resolve the security risks exposed by WPA2.
Protection against KRACKs: SAE considers devices as peers. Either party can initiate a handshake and send authentication information independently. Without the message exchange process, no opportunity is left for KRACKs.
Protection against offline dictionary and brute force cracking attacks: SAE directly rejects services for STAs that attempt to connect to the device for multiple times, preventing brute force or password cracking. In addition, SAE provides the forward secrecy function. Even if an attacker obtains the password in a certain way, the key is random each time a connection is set up. As a result, the attacker cannot decrypt the obtained data traffic because the key has been changed when the attacker attempts to reestablish a connection.
SAE enables individuals or home users to set Wi-Fi passwords that are easier to remember and provide the same security protection even if the passwords are not complex enough.
WPA3 SAE Modes
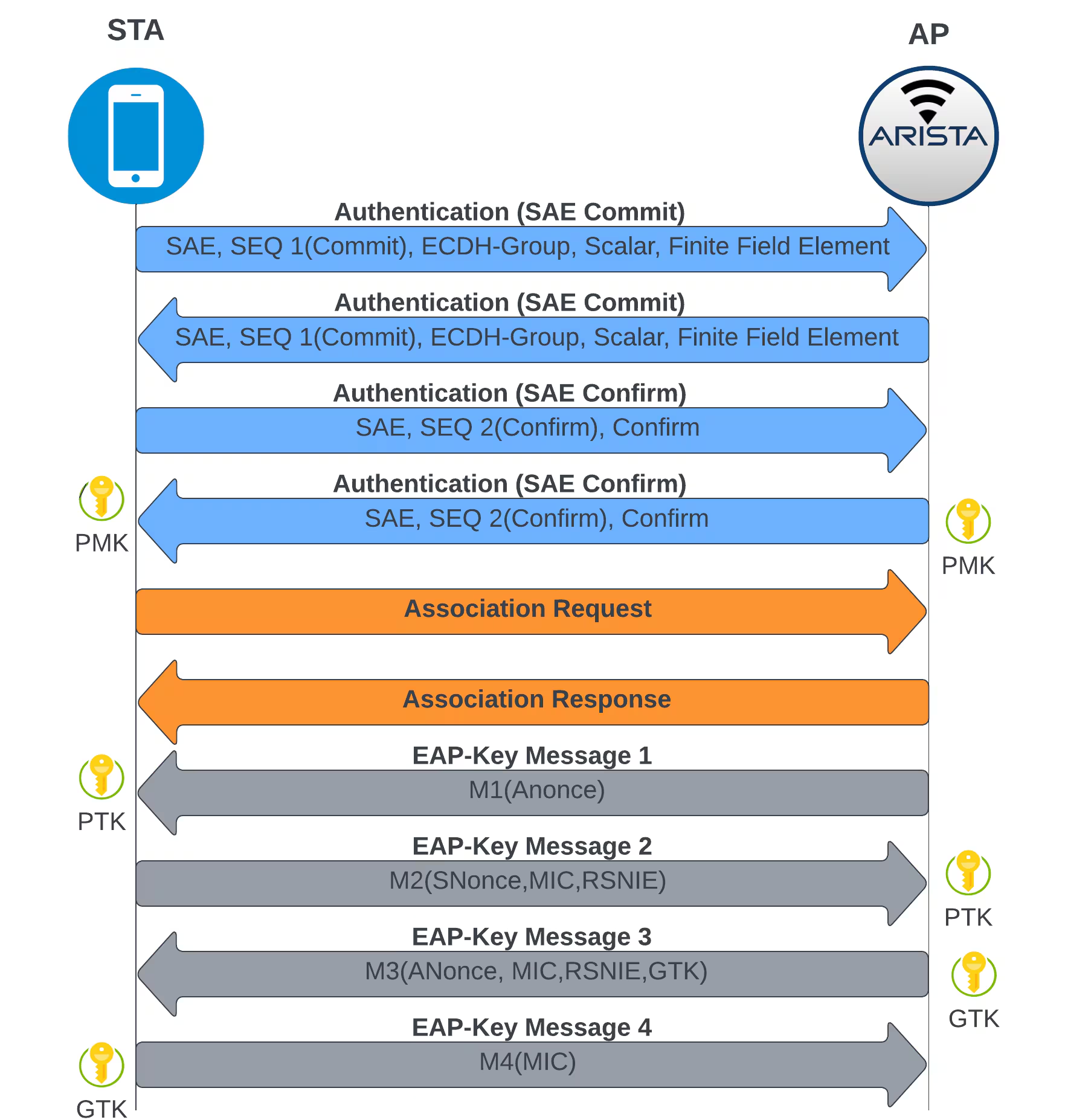
When compared with WPA2, WPA3-SAE uses two additional Authentication frames followed by Association Request/Response and then the 4-way handshake to generate the encryption keys as shown in image below
All four authentication frames (Two Commit and Two confirm) for WPA-3 SAE contain important information to calculate the PMK based on Elliptic Curve Cryptography (ECC). Let's unpack them below.
Authentication (SAE Commit)
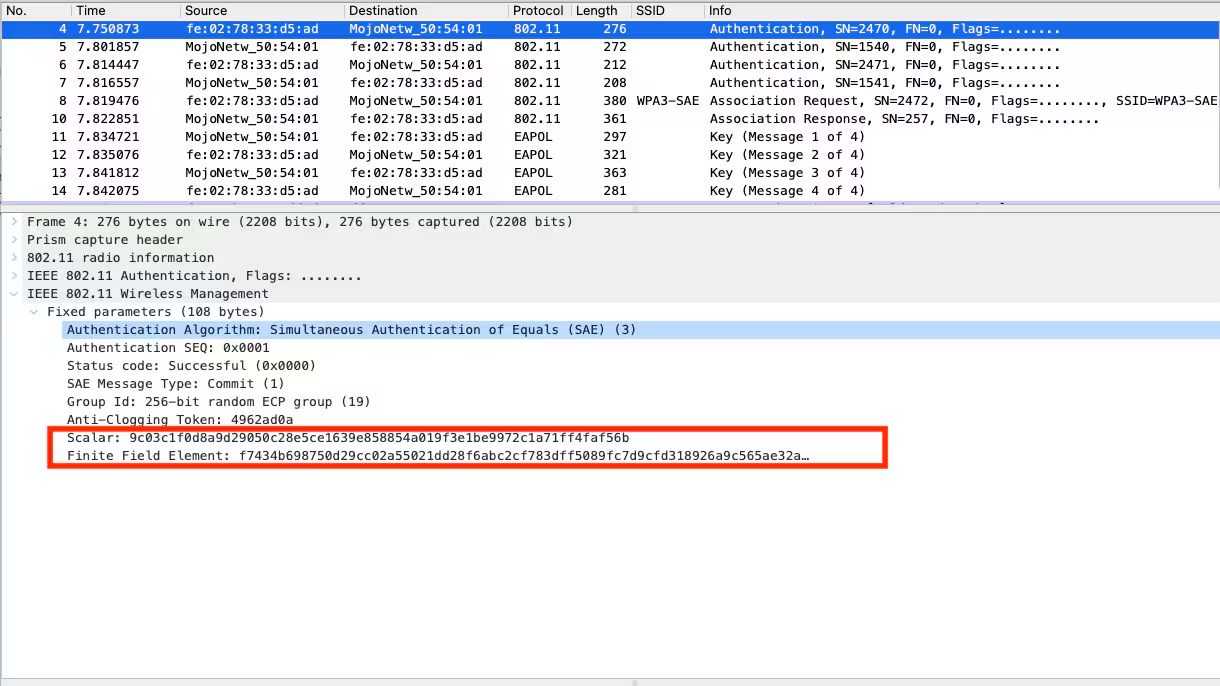
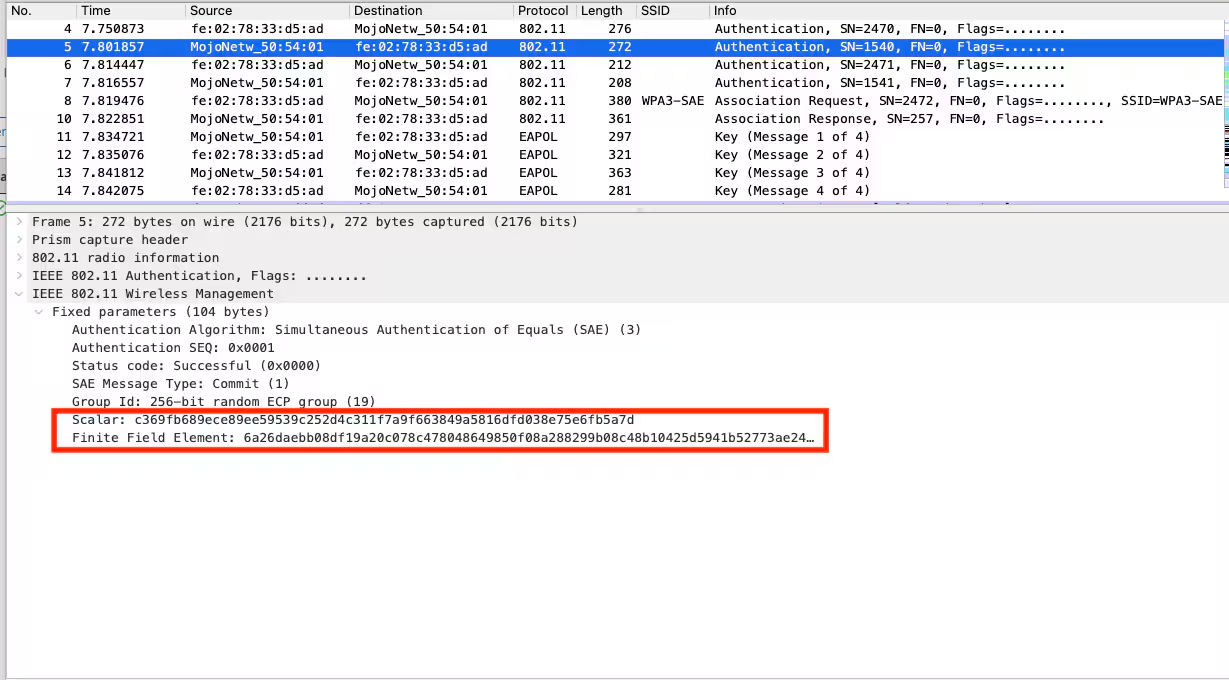
Wireless Station(STA) and Access point generates two random numbers Scalar and Finite Field Element which also contains the hashed passphrase from a known algorithm using Elliptic Curve Diffie-Hellman. Both parties send their Scalar and Finite Field element to the other one using the Authentication Commit as shown below
Along with the scalar and Finite Field Element, The Authentication commit frames from both the STA and AP also contain other common parameters such as
- Authentication Algorithm: Simultaneous Authentication of Equals (SAE) (3) - The Authentication algorithm number is 3 which is used for SAE, Other Algorithm numbers are (0=Open System, 1= Shared Key, 2 = Fast BSS Transition)
- Authentication SEQ: 0x0001 - The Authentication sequence Number 1 is used for SAE Commit frames and Authentication Sequence number 2 is for SAE Confirm frames
- Status Code: Successful (0x0000) - Showing a Successful status code
- Group Id: 256-bit random ECP group(19) - SAE uses Diffie-Hellman(DH) Key exchange in combination with a Prime modulus group or an Elliptic curve group to establish a secure connection over an unsecure medium, However WPA-3 Personal mandatorily uses Diffie-Hellman key exchange in combination with Elliptic Curve group(ECDH). There already exist some predefined curves as DH groups 19, 20 and 21. For example DH19 refers to the 256-bit elliptic curve which is selected as a minimum ECDH group for interoperability in SAE. DH20 refers to a 384 bit elliptic curve, while DH 21 refers to a 521 bit elliptic curve and higher Diffie-Hellman group numbers are usually more secure.
The Authentication Commit from the STA has an additional parameter named Anti-clogging Token which is used to provide some sort of defense to the flooding attacks with forged MAC addresses. The token is bound to the MAC address of the sender of an SAE Commit frame and the sender has to respond with the token in subsequent Commit frames. An attacker with forged MAC addresses will fail to do so or at least will have less flooding speed due to token calculation.
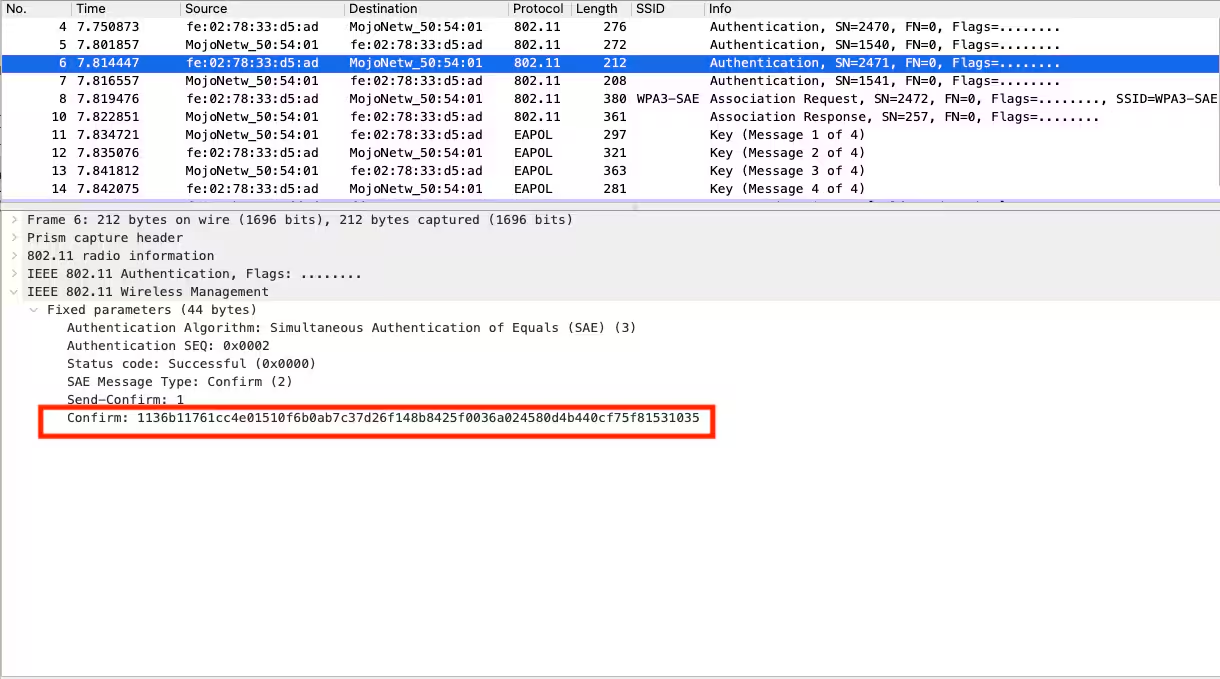
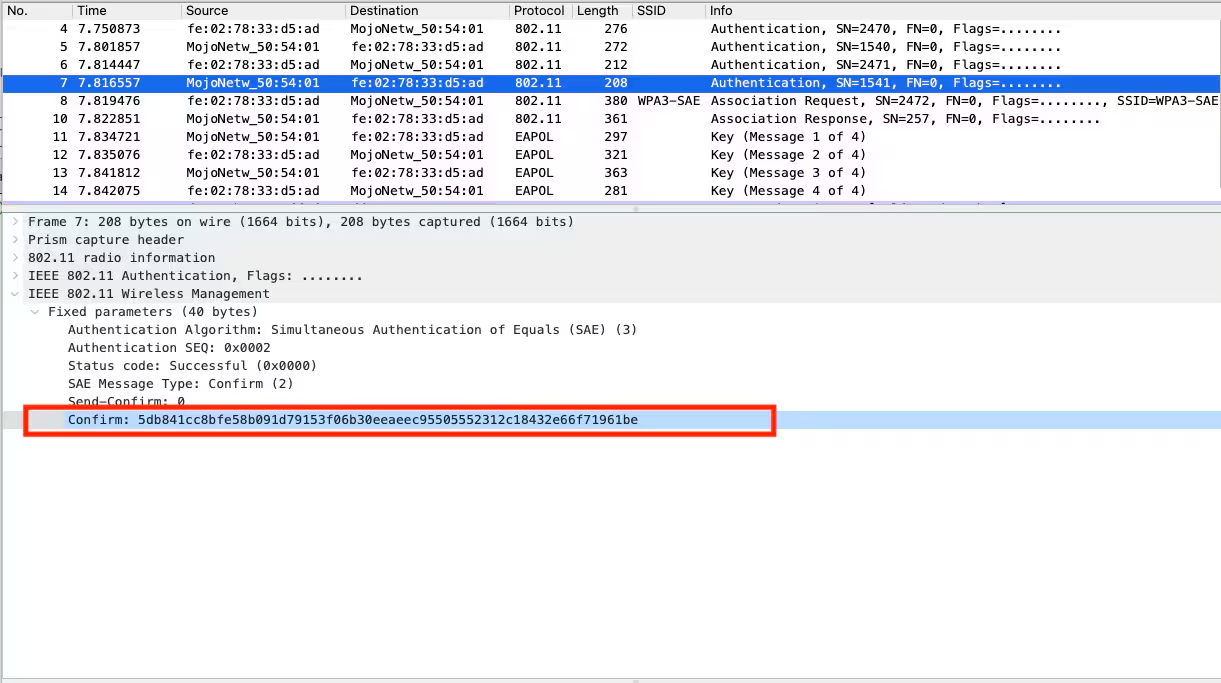
Authentication (SAE Confirm)
Both the Wireless STA and AP after receiving the Scalar and Finite Field Element from each other, calculate a hashed value and share them in the Authentication Confirm Frames as shown in below images.
From the above Authentication Confirm frames note that hash from the STA is not equal to the hash from the AP but both parties are able to verify the hash of the other party by calculating the hash themselves and compare it to the one they received. In case the hash could be confirmed the PMK is calculated.
It is important to know that this PMK is not based on the passphrase itself, but on scalars and Finite Field Elements that were calculated with random numbers, which only used a hashed version of the passphrase. Each time these random numbers change which also changes the Scalars and Finite Field Elements which in turn changes the PMK.
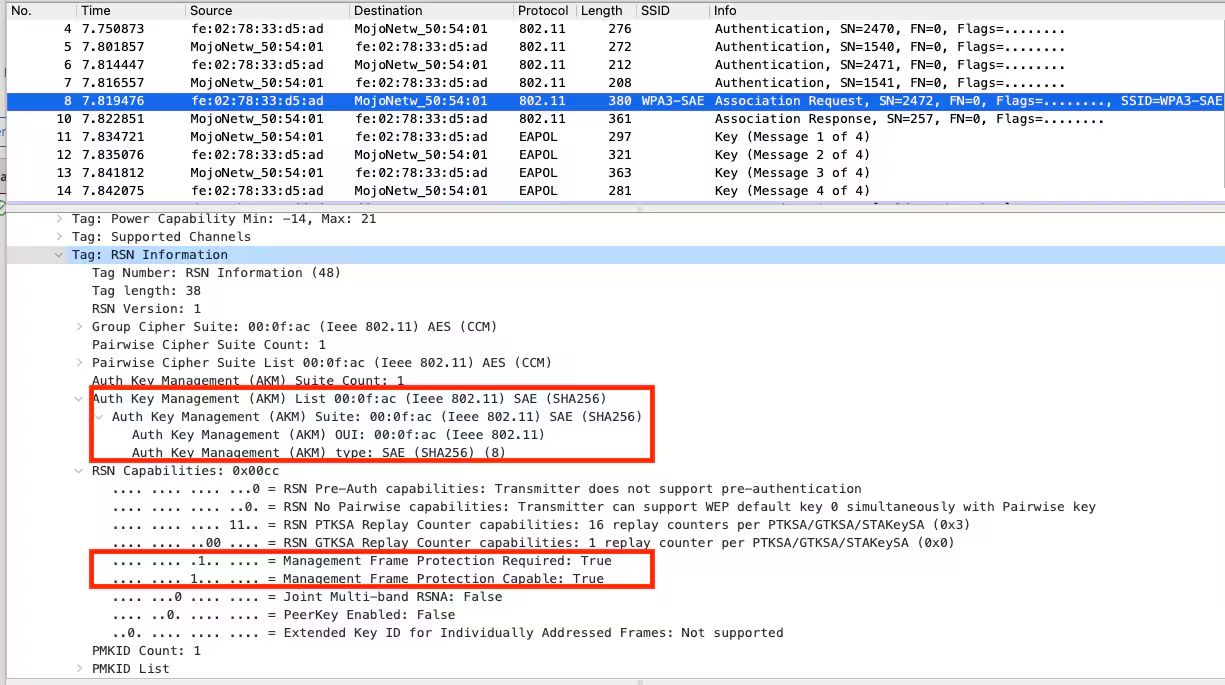
Thus with successful Authentication Confirm and Commit Frames, the STA and Client derives the PMK and Wireless STA sends the Association Request frame with AKM 00-0F-AC:8 which is used to indicate the SAE is in use, Note that the Management Frame Protection required and Capable is set to True in the RSN Capabilities of the Association Request
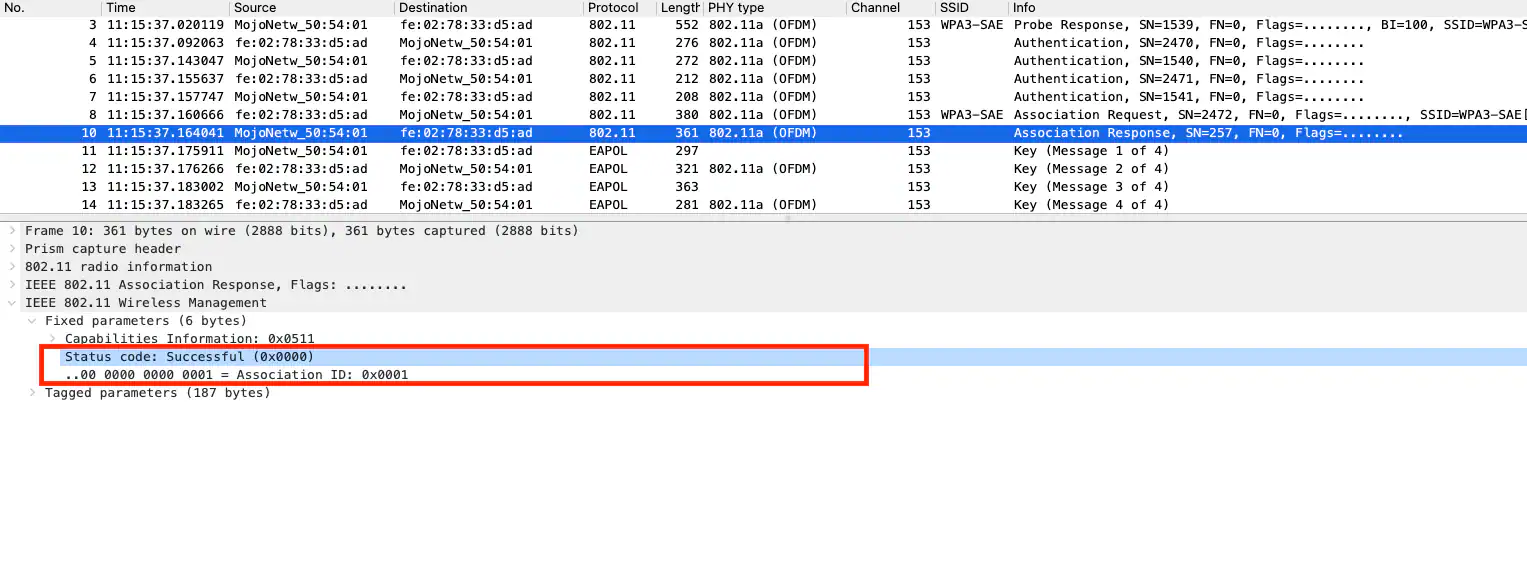
The AP then accepts the association request and assigns an association ID and status code shows successful as shown in the below Association response frame.
Thus with an established PMK, the AP and STA then go through a 4-way handshake to derive the encryption keys (PTK, GTK) and secure transmission between the AP and client are enabled.
WPA3 Transition Mode
The WPA3 transition mode allows both WPA2 and WPA3 capable clients to connect on the same SSID. This is implemented by broadcasting the beacons of the SSID configured with WPA3 Transition mode with both WPA2 and WPA3 capable as shown in the below image. The AP Advertises both the AKM suite types 00:0f:ac-6 for PSK and 00:0f:AC-8 for SAE however this makes the SSID only PMF optional and not PMF required mandatorily.
WPA3-Enterprise: Enhanced Security
Based on WPA2-Enterprise, WPA3-Enterprise provides WPA3-Enterprise 192-bit, a more secure optional mode. This mode provides the following security protection measures:
Data protection: The 192-bit Suite-B security suite is used. Compared with the 128-bit key used by WPA2, this suite increases the key length to 192 bits, further improving the password defense strength.
Key protection: The more secure HMAC-SHA-384 algorithm is used to export and confirm keys in the 4-way handshake phase. (HMAC: hash-based message authentication code; SHA: secure hash algorithm)
Traffic protection: The more secure Galois-Counter Mode Protocol-256 (GCMP-256) is used to protect wireless traffic after STAs go online.
Protected management frame (PMF): The Galois Message Authentication Code-256 (GMAC-256) of GCMP is used to protect multicast management frames.
OWE Authentication: Open Network Protection
Most Wi-Fi networks in public venues, such as airports, stations, and cafes, use the traditional open authentication mode. With OWE, users can access Wi-Fi networks without entering passwords, and data transmitted between users and Wi-Fi networks is not encrypted. This increases the risk of unauthorized network access.
WPA3 introduces an Enhanced Open network authentication mode for open networks. This allows users to access the network without entering the password, facilitating user access to the open Wi-Fi networks. Additionally, OWE uses the Diffie-Hellman key exchange algorithm to exchange keys between users and Wi-Fi devices, encrypting transmitted data and protecting user data security.
Documents
References
[1] https://info.support.huawei.com/info-finder/encyclopedia/en/WPA3.html
This post is licensed under CC BY 4.0 by the author.